
Introduction
In recent years, using ‘free’ public Wi-Fi has become a daily routine for many people especially working professionals. With the rise in public Wi-Fi usage, there has been an equal rise in Wi-Fi security threats and risks. One way to protect yourself while on public Wi-Fi is by using a VPN.
In this walkthrough, we will cover how to set up a Raspberry pi VPN router using OpenWRT and Private Internet Access VPN.
Requirements
In order to follow along, you will need the following:
- OpenWRT — https://openwrt.org/
- Raspberry pi 4 kit — https://bit.ly/3GZz8Jo
- Wi-Fi dongle — https://amzn.to/3FoAq0k
- PIA VPN (any VPN will do) — https://bit.ly/3H62fLf
- Standard Ethernet cable.
Step 1 — OpenWRT Install
The OpenWrt Project is a Linux operating system targeting embedded devices. Instead of trying to create a single, static firmware, OpenWrt provides a fully writable filesystem with package management. This frees you from the application selection and configuration provided by the vendor and allows you to customize the device through the use of packages to suit any application. For developers, OpenWrt is the framework to build an application without having to build a complete firmware around it; for users this means the ability for full customization, to use the device in ways never envisioned.~https://openwrt.org/
In our case, our target device is the raspberry pi 4B.
Step 1.1 — Download OpenWRT for raspberry pi 4b
Download the official OpenWRT raspberry pi 4b OS image from: https://openwrt.org/toh/raspberry_pi_foundation/raspberry_pi
Step 1.2 — Image OpenWRT onto the Raspberry pi sd card.
For this, we will be using Raspberry Pi Imager.

To select OpenWRT OS, click on CHOOSE OS` , select Use Custom then select the image you downloaded.

Select the relevant storage media i.e your sd card then write.


Step 2— Raspberry Pi OpenWRT Setup.
Before we configure the Pi to act as a router we need to:
Step 2.1 — Connect to the Pi
Insert the sd card to the Pi and connect an ethernet cable from the pi to your computer.

Your computer will automatically get an IP assigned to it from the Pi.
To check the up assigned you can use ifconfig

In my case the IP assigned is 192.168.1.219
If your computer hasn’t been assigned an IP you can manually set up your IP. By default, the PI’s Ip is 192.168.1.1. give your computer an IP in the same subnet for example 192.168.1.20.
Step 2.2— SSH to the Pi.
On your computer run.
ssh root@192.168.1.1`

Step 2.3 — Change the root password.
When logging in the first time it didn’t ask for a password which is very insecure. We need to set up a password for the root account.
To change the root password enter:
passwd root
Step 2.4 — Change the IP Range the PI assigns. (optional)
You can decide to change the IP range the Pi assigns to a less common private IP range.
To change the IP open the lan section of /etc/config/network and
- change
option ipaddr '192.168.1.1'tooption ipaddr '10.50.50.1' - add
option force_link '1'
vi /etc/config/network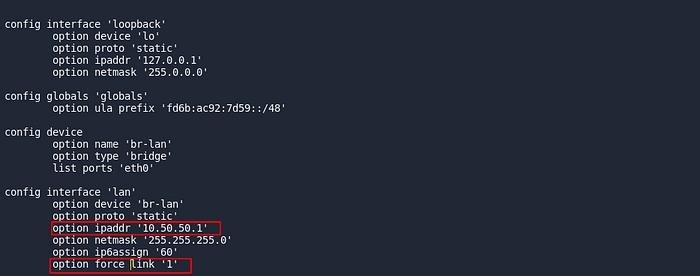
For the above changes to take effect we need to reboot.

To reconnect to the Pi, use the IP entered in /etc/config/network

Step 3— Connecting to the Public Wi-Fi
The next step is to connect the pi to the Public wifi network.
Step 3.1 — Create an interface to connect to the public wifi.
Edit /etc/config/network and add a new interface with the following properties.
config interface 'wwan'
option proto 'dhcp'
option peerdns '0'
option dns '1.1.1.1 8.8.8.8'The interface name is wwan
option proto ‘dhcp' is set so that the interface can use the IP assigned to it from the public access point.
option peerdns ‘0’ is set so that the interface can use an external dns.
option dns '1.1.1.1 8.8.8.8' specifies what dns servers to use.

Step 3.2 — Configure firewall
We need to let the wan network accept traffic. For this we need to edit the /etc/config/firewall file.
Open /etc/config/firewall and change option input` in wan zone from REJECT to ACCEPT .

Step 3.3 — Bring up the interface.
To bring up the interface edit /etc/config/wireless to
config wifi-device 'radio0'
option type 'mac80211'
option channel '7'
option hwmode '11g'
option path 'platform/soc/fe300000.mmcnr/mmc_host/mmc1/mmc1:0001/mmc1:0001:1'
option htmode 'HT20'
option disabled '0'
option short_gi_40 '0'
Commit the changes:
root@OpenWrt:~# uci commit wireless
root@OpenWrt:~# wifi
Step 3.4 — Connect to the wifi network.
Step 3.4.1: From your browser go to your Pi’s IP.

Step 3.4.2: Enter your username and password to login.

Step 3.4.3: On the Nav Bar select Network>Wireless.

Step 3.4.4: Click on scan on the first option to select the wifi network to connect to.

Step 3.4.5: Select the Replace wireless Configuration checkbox then enter your network passphrase then submit and save.


Step 3.4.6: Click on save and apply

Step 3.4.7: Test network connectivity using ping.

Step 4— Setting up an Access point.
In order to use the network from the Pi, we will need to set up an AP using the 2nd network card.
Step 4.1 — Download network card drivers.
Update the package manager using
opkg update
root@OpenWrt:~# opkg update
Install drivers
root@OpenWrt:~# opkg install kmod-rt2800-lib kmod-rt2800-usb kmod-rt2x00-lib kmod-rt2x00-usb kmod-usb-core kmod-usb-uhci kmod-usb-ohci kmod-usb2 usbutils openvpn-openssl luci-app-openvpn 
Step 4.2 — Enabling the secondary network card.
Plugin the network card and find it using lsusb

Enable the interface.
root@OpenWrt:~# ifconfig wlan1 up
root@OpenWrt:~# ifconfig

Step 4.3 — Configuring the Access point.
In order to use the AP, we need to configure the SSID and password.
Edit /etc/config/wireless radio1 section to:
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'scb/fd500000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0/usb1/1-1/1-1.3/1-1.3:1.0'
option htmode 'HT20'
option disabled '0'config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'vpnrouter'
option encryption 'psk2'
option key 'hardpassword'

option ssid ‘vpnrouter’ is the ssid name and option key ‘hardpassword’` is the password.
commit the changes
root@OpenWrt:~# uci commit wireless
root@OpenWrt:~# wifi
You can test the ap by connecting to it and pinging google


At this point you have a working router.
Step 5— Setting Up PIA VPN on the router.
Step 5.1 — Create VPN interface
Open /etc/config/network and add
config interface 'vpnclient'
option ifname 'tun0'
option proto 'none'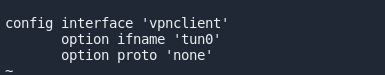
reboot
Step 5.2— Configure the VPN
Step 5.2.1 — Download an OVPN config file from PIA.
wget https://www.privateinternetaccess.com/openvpn/openvpn.zip
Step 5.2.2 — Copy the ovpn file to the pi using scp
scp pia.ovpn root@10.50.50.1:/etc/openvpn/client.conf

Step 5.2.3 — Install the necessary packages
root@OpenWrt:~# opkg update
root@OpenWrt:~# opkginstall luci-app-openvpn
root@OpenWrt:~# /etc/init.d/rpcd restart


Step 5.2.4-Set the Config parameters
root@OpenWrt:~# OVPN_DIR="/etc/openvpn"
root@OpenWrt:~# OVPN_ID="client"
root@OpenWrt:~# OVPN_USER="USERNAME"
root@OpenWrt:~# OVPN_PASS="PASSWORD"
Step 5.2.5 — Save username and password
root@OpenWrt:~# umask go=
root@OpenWrt:~# cat << EOF >${OVPN_DIR}/${OVPN_ID}.auth
${OVPN_USER}
${OVPN_PASS}
EOF
Step 5.2.6 — Configure VPN service
root@OpenWrt:~ #sed -i -e "
/^auth-user-pass/s/^/#/
\$a auth-user-pass ${OVPN_ID}.auth
/^redirect-gateway/s/^/#/
\$a redirect-gateway def1 ipv6
" ${OVPN_DIR}/${OVPN_ID}.conf
root@OpenWrt:~# /etc/init.d/openvpn restart
Step 5.2.7 — Provide VPN instance management
root@OpenWrt:~# ls /etc/openvpn/*.conf \
| while read -r OVPN_CONF
do
OVPN_ID="$(basename ${OVPN_CONF%.*} | sed -e "s/\W/_/g")"
uci -q delete openvpn.${OVPN_ID}
uci set openvpn.${OVPN_ID}="openvpn"
uci set openvpn.${OVPN_ID}.enabled="1"
uci set openvpn.${OVPN_ID}.config="${OVPN_CONF}"
done
uci commit openvpn
root@OpenWrt:~# /etc/init.d/openvpn restart

Step 5.2.8 — Configure firewall
root@OpenWrt:~# uci rename firewall.@zone[0]="lan"
root@OpenWrt:~# uci rename firewall.@zone[1]="wan"
root@OpenWrt:~# uci del_list firewall.wan.device="tun+"
root@OpenWrt:~# uci add_list firewall.wan.device="tun+"
root@OpenWrt:~# uci commit firewall
root@OpenWrt:~# /etc/init.d/firewall restart

Step 5.2.9 — Configure hotplug
root@OpenWrt:~# mkdir -p /etc/hotplug.d/online
root@OpenWrt:~#cat << "EOF" > /etc/hotplug.d/online/00-openvpn
/etc/init.d/openvpn restart
EOF
root@OpenWrt:~#cat << "EOF" >> /etc/sysupgrade.conf
/etc/hotplug.d/online/00-openvpn
EOFStep 5.2.10 — Test the vpn.
If you open the VPN tab in the browser you will find the new vpn client we’ve configured

To test the vpn we can open https://www.dnsleaktest.com/

According to the dnsleak test I am in Zurich, Switzerland which is not the case.
Conclusion.
VPNs are one way of protecting yourself while on public internet but the best way is to stay safe is to avoid networks you don’t own.
